SaaS Goals 2023: Reduce Software Risk via Threat Modeling Automation (Part 1)
- Ayomide Odukoya
- Dec 19, 2022
- 4 min read

The start of a new year is often a reset, a welcome refresh. We set goals and strive to reestablish ideals. But the goals that stick are the ones that we truly believe are essential. For businesses, especially startups, healthy revenue growth is essential. Cybersecurity readiness has become a foundational part of the revenue picture; either boosting customer trust, or eroding it. This is certainly true for SaaS companies whose product(s) are always online, accessible 24/7, and exposed to cyberattacks. For SaaS startups, security often comes late i.e. after the platform is built, an audit is done. Apart from being an afterthought, which makes it less effective, that's the most expensive way to implement security in a software product. You end up redoing lots of work to address security gaps and mistakes.
What if you could identify security risks early, while designing and conceptualizing your software products or its features? You would be able to lower the cost of implementing your product by simultaneously addressing the security concerns that are relevant to your product and business. That will be a 2023 goal worth executing.
Some of the techies already know where I'm going:)) - threat modeling! You can skip right on to the automation section, if you're already familiar with threat modeling.
What is Threat Modeling?
Threat modeling, according to NIST, is a method of risk evaluation that simulates the attack and defense sides of a logical entity, such as a piece of data, an application, a host, a system, or an environment. Threat modeling is a crucial and effective method that needs to be integrated into the security development lifecycle of an organization. Threat modeling has been integrated into the software development lifecycle by large/enterprise organizations over the years, but this is not the case for many startups or small-scale businesses because some parts of the process require engineers to have strong software security skills or businesses must hire security architects, who may be expensive.
Automating Threat Modeling - Empowering Startups and SMBs
Resilient recognizes how effective and influential threat modeling is and how costly it may be for small-to-medium scale businesses to integrate it into their development lifecycle. For this reason, we are writing on free/community editions of threat modeling automation tools in this article to make it easier to integrate threat modeling into your developmental lifecycle. Many threat modeling tools have been introduced in the Security field over the years, including the “Threat Modelling Tool” from Microsoft, the "Threat Dragon" from OWASP, IriusRisk, ThreatModeler, threagile, and many more.
In this 2-part series, we have decided to focus our lens on two of the most extensive tools in this space, which are IriusRisk and ThreatModeler. These tools provide automated threat modeling Software-as-a-Service (SaaS). They enable you to build a component interaction plus data flow representation of your product's architecture, utilizing "Click-and-Drag" supported by their extensive lists of available software and cloud architecture components. They also leverage standard security frameworks and benchmarks as their sources for deriving security best practices. This means that the architecture diagrams you create via those IriusRisk or ThreatModeler are converted into software threat models that identify:
the data you should protect.
the threats or attacks that you should watch out for.
the interfaces or places in your products where those threats are relevant.
the mitigations that address those threats.
Threat Modeling with IriusRisk
Let's demonstrate how simple it is for you to begin your threat modeling journey via IriusRisk.
1. Creating Your Threat Model Project
You can access the free community edition of the IriusRisk platform by clicking this link to sign up and log in.
Once you're in, you are presented with a Projects Page where you can create a new project and view a list of all the projects that have ever been created after successfully creating an account and logging in.

IriusRisk Projects Page
After a project has been created, you are shown a screen where you can start building your Threat Model Diagram by putting together the architecture of your application using an extensive list of components, including components from well-known Cloud Services Providers like Amazon Web Services, Microsoft Azure, and Google Cloud Platform.

2. Building A Threat Model (or Software Architecture) Diagram
Building a threat model diagram requires an understanding of the concepts of Trust Zones and Components. TrustZones as the name implies, are simply boundaries within the components.

3. Reviewing Identified Threats and Proposed Defenses
IriuRisk develops a list of threats and defenses for each component placed in the threat model diagram in the background, and this list can be tracked and viewed in both the threats and countermeasures sections of the program, as shown below.
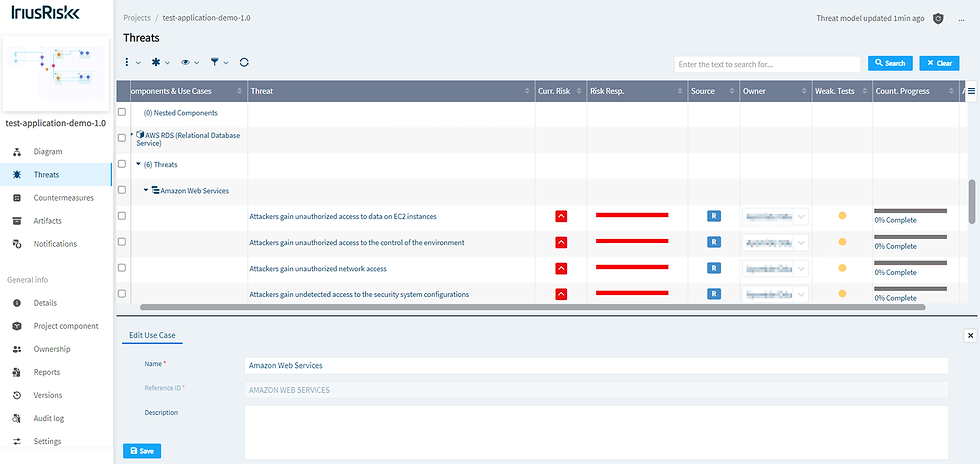
Threats are ranked in the threats section according to the components they affect, their risk assessment, their risk response, or their use cases. Applying different standards or frameworks to your threat model, such as the PCI-DSS, CIS Benchmarks, and a few others, may change or impose stricter requirements or countermeasures for your product. This is another important activity that may be accomplished in this section. Threats against the project generally or streamlined against a specific component can be manually added by the user if they are not already included in the list of threats provided by IriusRisk.

A list of countermeasures is provided in the countermeasures section for each threat outlined in the threats section. These countermeasures can either be applied to each component individually or as a list of best practices recommended by Cyber Standards or frameworks. Issue tracking and synchronization with project tracking tools like Jira, ServiceNow, or Azure DevOps are both accessible from this section.
Threats can be classified as being mitigated, not mitigated, or not applicable to the project.
4. Generating Compliance Reports
After all countermeasures have been validated, a report in PDF format can be generated from the Reports section, as shown below.
Conclusion
This tutorial demonstrates the effectiveness of IriusRisk's community threat modeling platform. We will examine Threatmodeler in the next post in this series.
***
The FREE 5-Minute Security Assessment for Startups ™
I hope you found this article helpful. If you're a SaaS startup leader, please check out our Free 5-Minute security assessment, designed specifically for software startups. Yes, it really does take you only 5 minutes, then we do the rest. Once you complete the assessment, we craft two confidential reports - A Security Assessment report that shows where you are with software security and your score, and A Security Recommendations Report with custom solutions that your team can either begin implementing or add to your roadmap.
Happy Holidays:))! ❤️

Comments